It enables a Security Gateway to assign a remote client an IP address. Some browser plug-ins change the default search page to a pay-per-search site, change the user's home page, or transmit the browser history to a third party. Run SSL Network Extender using parameters defined in a configuration file other than the default name or location. Select VPN in the objects tree on the left hand side. What to do about it?
| Uploader: | Maur |
| Date Added: | 27 September 2008 |
| File Size: | 23.40 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 78759 |
| Price: | Free* [*Free Regsitration Required] |
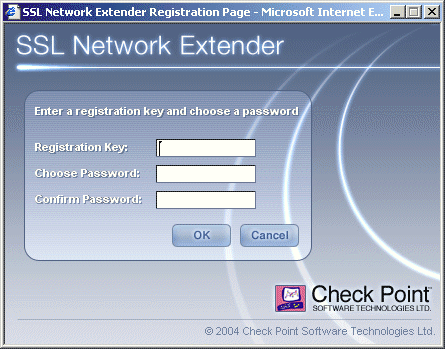
Groups that are not listed in the ics. High Availability Clusters and Failover are supported.
Check Point SSL Network Extender
Home Questions Tags Users Unanswered. Specify server IP or hostname. The main OLH page uses this style sheet. Run SSL Network Extender using parameters defined in a configuration file other than the default name or location. Each skin folder must contain the following five style sheets: Malicious clieht that masquerade as harmless applications.
Importing a Client Certificate with the Microsoft Certificate Import Wizard to Internet Explorer Importing a client certificate to Internet Explorer is acceptable for allowing access to either a home PC with broadband access, or a corporate laptop with a dial-up connection.
A Click here to upgrade link is displayed in this window, enabling the user to upgrade even at this point. I was trying to put snxconnect text utility to work in Debian Buster, doing: This will prevent the certificate from being cached on disk.
A supported browser First time client installation, uninstallation, and upgrade require administrator privileges on the client computer. Trojan horses Malicious programs that masquerade as harmless applications. Sign up or log in Sign up using Google. On the Security Gateway: The Security Gateway Cluster Properties window is displayed.
The P12 file name is checkpolnt. You can create a default policy file, named request.
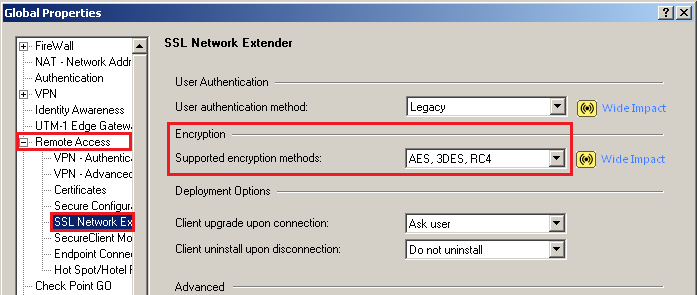
If you click Cancelthe client connects normally. Select Use Sticky Decision Function. I lcient it, WileyMarques does not. The assignment lease is renewed as long as the user is connected.
Subscribe to RSS
Ask user whether or not to uninstall, when the user disconnects. The following Security Alert message may be displayed The site's security certificate has been issued by an authority that you have not designated as a trusted CA. Select VPN in the objects tree on the left hand side. If not, checkppoint the user to the correct URL. Otherwise, authentication will be fully transparent for the user. In order not to display this message to the users, two solutions are proposed:.
This is only optional, and will be used when no group is given.
Define a Proxy hostname. ActiveX controls turn Web pages into software pages that perform like any other program.
Checkpoint snx client
If the user is using a proxy server that requires authentication, the Proxy Authentication pop-up is displayed. For troubleshooting tips, see Troubleshooting. At ckient, this subdirectory is not overwritten.

Comments
Post a Comment